Avast Threat Labs has discovered a new Hungarian ransomware sample that is imitating Locky.
At Avast Threat Labs, we are constantly monitoring the threat landscape and evaluating current risks. Most of the time, we face prevalent strains of malware, such as Locky or Cerber ransomware, but from time to time we are alerted by our automated systems about anomalies within active in-the-wild samples. These alerts are either new techniques used by known malware or a discovery of a new strain.
This is a short story about our discovery of “Hucky” ransomware.
Detecting a new threat
A few days ago, our systems notified us about a new ransomware sample that we are detecting and blocking. Based on a behavioral report from our sandbox, this sample attempts to encrypt user files and append a '.locky' extension to their names. Locky ransomware immediately came to our mind, but we quickly realized it is not Locky, because Locky is no longer using the .locky extension name. Furthermore, most of the common Locky-specific indicators of compromise (IOCs) are not present in this sample. Therefore, it caught our attention and we started digging deeper and analyzing this particular ransomware sample.
Locky lookalike
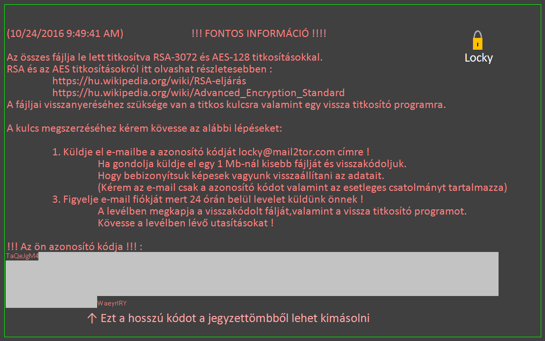
We tried executing this sample in a virtual machine and let it run in a safe environment. At the end of the execution, the machine looked as follows.
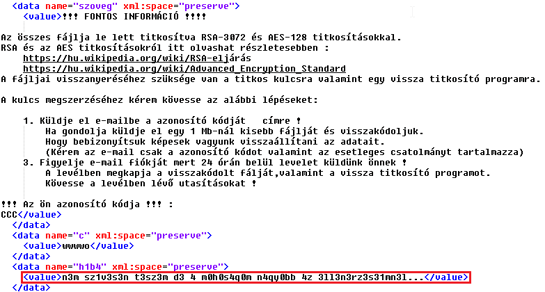
New wallpaper:
Displayed text with ransom payment instructions:
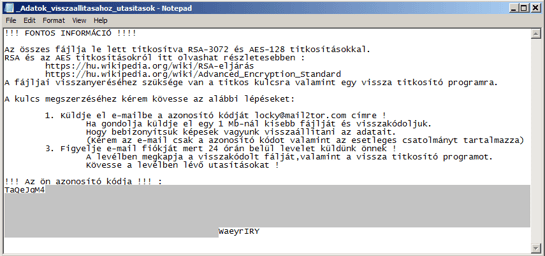
Our decoy files were encrypted and renamed:
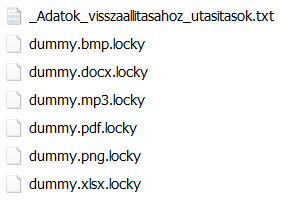
If you have seen a machine infected by Locky, it probably looked very similar: new wallpaper with ransom instructions (rendered with the same font and colors as the one above), the same text displayed once again in Notepad, and, most importantly, the files were encrypted and renamed to file name + “.locky”.
But just because this new sample looks like Locky, and calls its files Locky doesn’t mean it’s Locky!
We've been previously written about ransomware strains that mimic more "successful" strains to increase their chances of getting ransom payments and this is yet another one.
Based on the following leads, we have named this one Hucky, which is an abbreviation for Hungarian Locky. When we put both these strains side by side, we can see several differences:
- Locky no longer uses the '.locky' extension. As I write this blog post, it uses “.shit” (please excuse the language, but malware authors are not always polite…) and “.thor”:

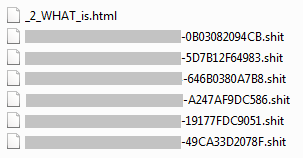
Above is an example of encrypted files – Hucky (top) and Locky (second image).
- The encryption process is quite similar in both versions: the randomly generated AES key is used for file encryption. This key is further encrypted by a public RSA key. However, Locky retrieves its public key from a C&C server (in most of its versions), whereas Hucky uses a hardcoded one. This allows Hucky to operate offline.
- Two features unique to Hucky are: displaying a dummy Word document while encrypting files, most likely to give victims something to do while their files are being encrypted, and a system restart right after the encryption process is finished. Hucky’s authors may restart computers after the encryption process to delete the program itself and thus hide any hints that may help anyone figure out the decryption key.
- Locky's ransom instructions are in English and they are available (at the moment) as HTML files, while Hucky displays its instructions in Hungarian and as text files. Furthermore, Locky requests a Bitcoin payment via one of the Tor pages it provides, while Hucky requires victims to send an email to a provided Mail2Tor address.
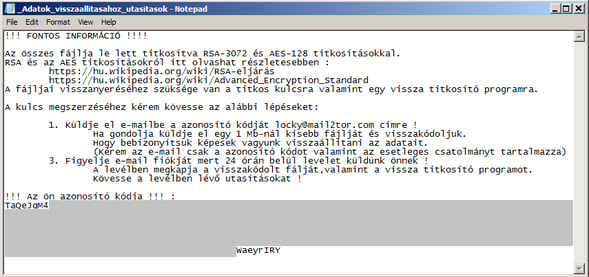
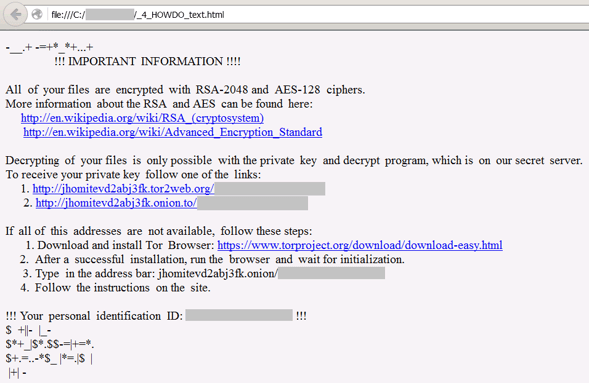
Above: Ransom instructions – Hucky instructions (top) and Locky instructions (second image).
- The images used for replacing victims’ wallpaper are visually very similar at a first glance. However, in Hucky, Hungarian is once again used instead of English. Furthermore, Hucky's image also contains a low quality symbol of a yellow padlock, which Locky’s ransom screen doesn’t have.
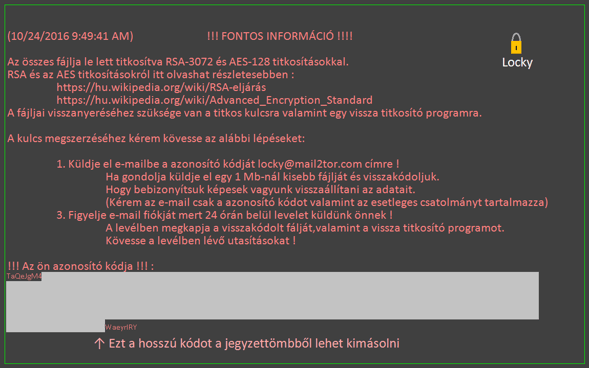
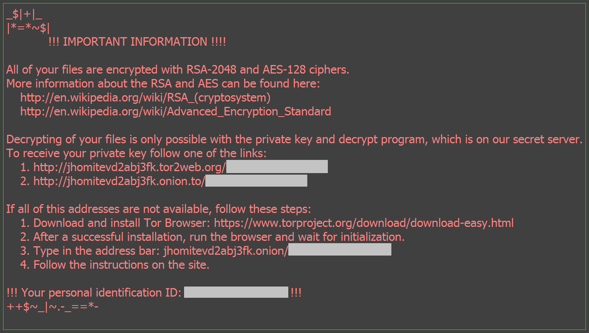
Above: Wallpapers with ransom instructions – Hucky wallpaper (top) and Locky wallpaper (second image).
- The list of files and extensions targeted by Hucky contain 200 items, which is only about half the size of the list used by Locky. In addition to traditional formats targeted by ransomware, Hucky also targets video game files, such as ones used by StarCraft2, World of Tanks, or Minecraft.
- Another difference is the programming language: Locky was created using Microsoft Visual C++, while Hucky is based on Microsoft VisualBasic.
Hungarian roots
As we found out during our analysis, Hucky has a significant Hungarian footprint.
All of Hucky's interactions with victims are done in Hungarian. Furthermore, Hucky's executables are spread with Hungary-related names, such as semmi.exe (Hungarian word for nothing) or turul.exe (name of a Hungarian national symbol).
Moreover,Hungarian is also used in Hucky's code, such as namespaces, names of methods and variables, etc.
An example can be seen in the following image. The highlighted text is a mixture of Hungarian and L33t speak. It can be loosely translated as authors confession: “I hate to do this, but I like the money”.
Another lead of Hucky's origin are the so-called PDB debug strings that are automatically inserted in executable files by compilers. These strings can reveal the username of author as well as project name:
The earlier version (compiled on 2016-10-04):
C:\Users\Dani\Desktop\nocrime\nocrime\obj\x86\Debug\turul.pdb
The later version (compiled on 2016-10-06):
C:\Users\user\Desktop\kalosip\titkoss\obj\x86\Debug\mgtow.pdb
In our case, the authors username was originally 'Dani' (probably Dániel). A few days after releasing the initial version, the author started hiding the username via a generic 'user' account. Another interesting piece of information is revealed by the project name, “titkoss”. This might come from the Hungarian word “titkos”, which can be translated as “secret”. This means the author is not only using Hungarian as a communication language with its victims, but he or she is using it for internal naming.
Furthermore, the Hungarian texts don’t seem to be machine translated (although they contain some spelling errors).
Conclusion
We can conclude that Hucky is a new ransomware strain currently targeting Hungarian users only. Based on the aforementioned leads, there is a fair chance that its author is a native Hungarian speaker. The Hungarian orientation is probably also the reason why Hucky’s prevalence is low at the moment. Finally, we should mention Hucky's undisguised effort to look like Locky.
We'll be monitoring this threat and inform you about its changes or increased prevalence. In the meantime, stay safe:
- Don‘t open suspicious attachments (e.g. .doc, .xls, and .zip files)
- Disable Microsoft Office macros by default and never enable macros in strange/unknown attachments that you receive via email
- Keep recent backup copies of important data in a secure place either online or offline
- Ensure that your system and applications are fully updated and patched
- Make sure you have antivirus (we like to recommend Avast :-) ) installed and actived on your PC and mobile devices
Indicators of Compromise
SHA256:
02766dd4934a90f8cdb5a715e0de30ea31cb57c9ec30cc77bca16ea9c3318be4
24b1b132b6a15bebce2934fe562f03ba62ca4db432ed566339012774f7bc7818
5ba291a4aa34c177d4e41f6ed818ef3d6c383dc5406adb2e12eb3c648c2f52eb
613b76e0d6ccd1d05a39ef0c4c48293a8800ebc2587b87218a8328b8af3c4109
6c9b0934f22e8265876b1d0aba18f0efe68a733e83c892db109af83348c0901f
7f71949cdfb0981f64eaaae9b3c9fdc68dc31bae97fac6306597f010637054f2
8f912771316d589be797feb1c2c5d2fd820c833f3c131760424b79aef76e2000
cbdec0f2fdf8c52f36b8baa0ea772bb18021a839ac856dd656f9effc3c30b64d
Files:
_Adatok_visszaallitasahoz_utasitasok.txt
_locky_recover_instructions.txt
\Startup\mgtow.exe
\Startup\Java Update.exe
\Startup\Fontos Informacio.bmp
\Temp\monodocu.dat
\Temp\d3m4g0g.dat
/\\Temp\\[A-Za-z0-9]{6}\.bat$/